Cybersecurity
Dynamics of a never-ending quest
By Stephen Metzger PhD Economist, and Adjunct Professor of Maritime Economics, Fordham University
 The quest for making computer systems of the maritime industry – and all they control – secure against illicit and dangerous intrusions is never-ending. This is the case because human ingenuity is diligently at work in a game of strategy and deception, where the payoffs can be in the billions of dollars – as illicit gain or loss avoidance.
The quest for making computer systems of the maritime industry – and all they control – secure against illicit and dangerous intrusions is never-ending. This is the case because human ingenuity is diligently at work in a game of strategy and deception, where the payoffs can be in the billions of dollars – as illicit gain or loss avoidance.
In the movie, “Catch Me If You Can”, starring Leonardo DiCaprio and Tom Hanks, you will recall the extraordinary ability of Frank Abagnale Jr, the real-life man DiCaprio portrays, to impersonate and deceive supposed peers, ranging from doctors to airline pilots.
Abagnale, now a security consultant, makes two key observations: First, technology has actually facilitated the perpetration of fraudulent schemes. Second, all cybercrimes are enabled by someone who did something wrong, or failed to do something he or she should have done.
Focused
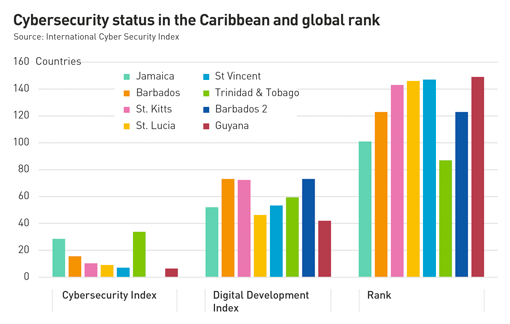
While not specifically focused on maritime sector, the National Cyber Security Index (NCSI) is a reasonable gauge of cybersecurity status among island nations in the Caribbean. It is useful to get an indication of where the region stands relative to other countries in the world, particularly island nations. See graph below.
Eight countries in the Caribbean Basin are depicted in the graph, showing their respective indices of cybersecurity, digital development and rank among the 160 countries for which data is collected. The region has an average rank of 127 (the higher the ranking the lower are the cybersecurity capabilities) out of the aforementioned total of 160 countries in the index. A selection of other small island economies, including Singapore, Iceland, and Cyprus had a much lower average score of 49.
The data illustrated clearly suggests the need to raise cybersecurity capabilities of the region. Cybersecurity proceeds at two levels: The individual business or public entity, a micro perspective and a collective, or macro, effort aimed at promulgating and enforcing community-wide protocols. Employee (and public) awareness of potential breaches of security is critical for developing effective systems of cybersecurity. Abagnale’s admonition cited above is mirrored in the words of Cynthia Hudson, CEO, and her team at HudsonAnalytix, a cybersecurity consultancy, based in Cherry Hill, New Jersey: “Awareness is the first step,” she stresses. “Without an awareness of the threat and the extent of it, there is little incentive to investment in cybersecurity – and what is invested will have little impact.”
The second step Hudson notes is the need for an assessment. Because cyber threats adapt and evolve, a cybersecurity protocol must be based on an ongoing assessment. An assessment implemented five years ago, is unlikely to stand the test of sophisticated hackers of today.
Third step
“Education and training provide the third step of building an effective cybersecurity system,” Hudson emphasized. Team member Marc Smith, Chief Operations Officer, adds, “Almost all breaches of security start with an unguarded response to a seemingly innocuous, routine inquiry from a hacker.”
Andrew Baskin, Vice President and General Counsel at HudsonAnalytix, cites the example, all too common, that once a hacker becomes part of the network of contacts within the company data base, the hacker can at an opportune time submit a fake invoice that is errantly processed by accounts payable. After the first three steps in building the firewall, implementation is a combination of using the investment in human capital and the requisite software, to activate the system. Importantly, the full system is composed of both the investment in human capital and physical capital (the software and hardware). The one will not work well without the other.
It is axiomatic that cyber threats need a collective, or macro response—companies, agencies, and governments working together to coordinate their cybersecurity efforts. In this regard, I interviewed Juan Carlos Croston, President of the Caribbean Shipping Association (CSA) to draw upon his perspective as its chief executive.
Croston notes there is yet insufficient incentive within the industry for companies, ports, and government agencies to coordinate their cybersecurity efforts. The issue is often one of reluctance to divulge proprietary or competitive information. Further, entities within the industry may be hesitant to make significant changes to their IT system, fearing a major disruption of the system. “Although these obstacles can be overcome, a foundational system of cybersecurity has yet to be put in place – one that is sustainable over the long term and is permanent in structure and platform attributes,” Croston concludes.
The CSA has a major role in two areas, education and advocacy, both of which come into play with the cost of investment in cybersecurity – particularly given the Covid-19 crisis. Croston explains, however, that, “Initial investments in cybersecurity don’t need to be, and shouldn’t be, in expensive technologies. Addressing personnel and processes are the first priority.”
Insurable
Croston discussed the possibility of cybersecurity insurance. He notes, however, this requires “insurable” organizations that have achieved a level of cybersecurity maturity, at which point insurance companies will offer such services.
Collective security starts with individual efforts at the micro level, guided by the comprehensive perspective of macro level (i.e., inherently collective) organizations, such as the CSA and its broadly-based membership.